Cloud HSM
A hardware security module (HSM) is a dedicated crypto processor that is specifically designed for the protection of the crypto key lifecycle by securely managing, processing, and storing cryptographic keys inside a hardened, tamper-resistant device. AWS Offers managed HSMs.
Compliances:
-
FIPS 140-2 Level 3
-
PCI-DSS
-
PCI-PIN
-
PCI-3DS
-
SOC2
Cloud HSM can integrate with KSM by using it as a custom key store in KMS.
Cloud HSM provides End-to-end Encryption that is NOT visible to AWS.
Cloud HSM Vs KMS
The difference is thin but important, especially if there’s compliance involved.
Tenancy
KMS uses HSM modules but while KMS uses HSM modules shared with other accounts, Cloud HSM allows you to rent a dedicated, Single Tenant, HSM unit for you exclusively.
Management
AWS has a certain level of access to KMS, whereas on Cloud HSM you are on your own because they only manage the provisioning and maintenance of the appliance, AWS have no access to the parts of the hardware/software where keys are stored.
If you lose access to the HSM, AWS can’t help.
Access
While KMS is accessed using standard AWS APIs (via console, SDK, API directly, CLI, …), Cloud HSM is accessed using industry standard APIs via the AWS CloudHSM Client SDK:
-
PKCS#11
-
Java Cryptography Extensions (JCE)
-
Microsoft CryptoNG (CNG) and Key Storage Providers (KSP) libraries
-
OpenSSL Dynamic Engine
Loose integration with AWS services is by design.
Architecture
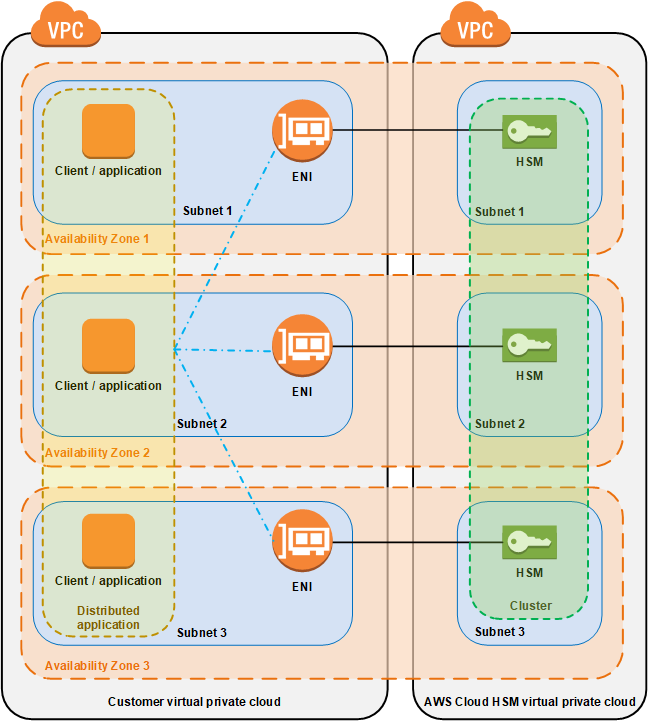
Cloud HSM is a regional services that supports High Availability in different AZs (not all AZs may support it). To enable HA you need to create a cluster.
The actual Cloud HSM instances reside in an AWS managed VPC, but those instances are accessible from your VPC using ENIs (one in each AZ).
In order to set up high availability, it is your responsibility to configure your application to load balance traffic among available ENIs in each AZ. Application connect to ENIs using the Cloud HSM SDK or, if you use bare instances you can use the Cloud HSM Client Utility (CMU) or the CloudHSM CLI.
Use Cases
-
TLS/SSL processing offload for web servers, which is much more economical and efficient than having EC2 instances or containers do it.
-
Transparent Data Encryption (TDE) for Oracle databases
-
Protect the private key for an issuing Certificate Authority
-
Leverage the benefits of AWS CloudHSM and AWS Key Management Service: Customers can combine AWS CloudHSM and AWS KMS to store key material in a single-tenant environment that is FIPS 140-2 Level 3 certified while also getting the key management, scaling, and cloud integration benefits of AWS KMS.
-
Achieve regulatory compliance
-
Encrypt and decrypt data
-
Sign and verify documents with private and public keys
-
Authenticate messages using HMACs and CMACs
-
Generate random numbers