AWS Control Tower
AWS Control Tower allows for quick and easy setup of multi-account environments, following prescriptive best practices, far beyond what Organizations alone can do, because it actually orchestrates multiple services (including AWS Organizations).
It can be used to detect configuration drifts.
For example it leverages:
-
Organizations
-
IAM Identity Center
-
CloudFormation
-
AWS Config
-
SNS
-
more…
In general it provides:
-
Automated account configuration
-
Centralized governance
-
Extensibility
Components
Landing Zone
It’s the enterprise-wide container that holds all of your organizational units (OUs), accounts, users, and other resources that you want to be subject to compliance regulation.
It provides:
-
SSO and ID Federation (via IAM Identity Center)
-
Centralized logging and auditing (via CloudWatch Logs, CloudTrail, AWS Config and SNS)
It has the concept of Home Region, the region initially used for Control Tower. You can explicitly allow or deny the usage of other AWS regions but the home region is always available.
Controls (Guardrails)
They detect drifts or mandate rules and standards across all AWS accounts within the landing zone.
Types of Guardrails:
-
Mandatory: always applied
-
Strongly Recommended
-
Elective
Guardrail modes:
-
Preventive: they prevent configuration from being applied if it conflicts with them.
These are implemented using SCPs, for things like:-
Allow/Disallow the usage of certain AWS Regions
-
Prevent chenges to bucket policies
-
-
Detective: they highlight a drift from compliance while allowing the violating configuration to be applied. For example:
-
Warn when an EC2 instance with a public IP address is created.
-
Architecture
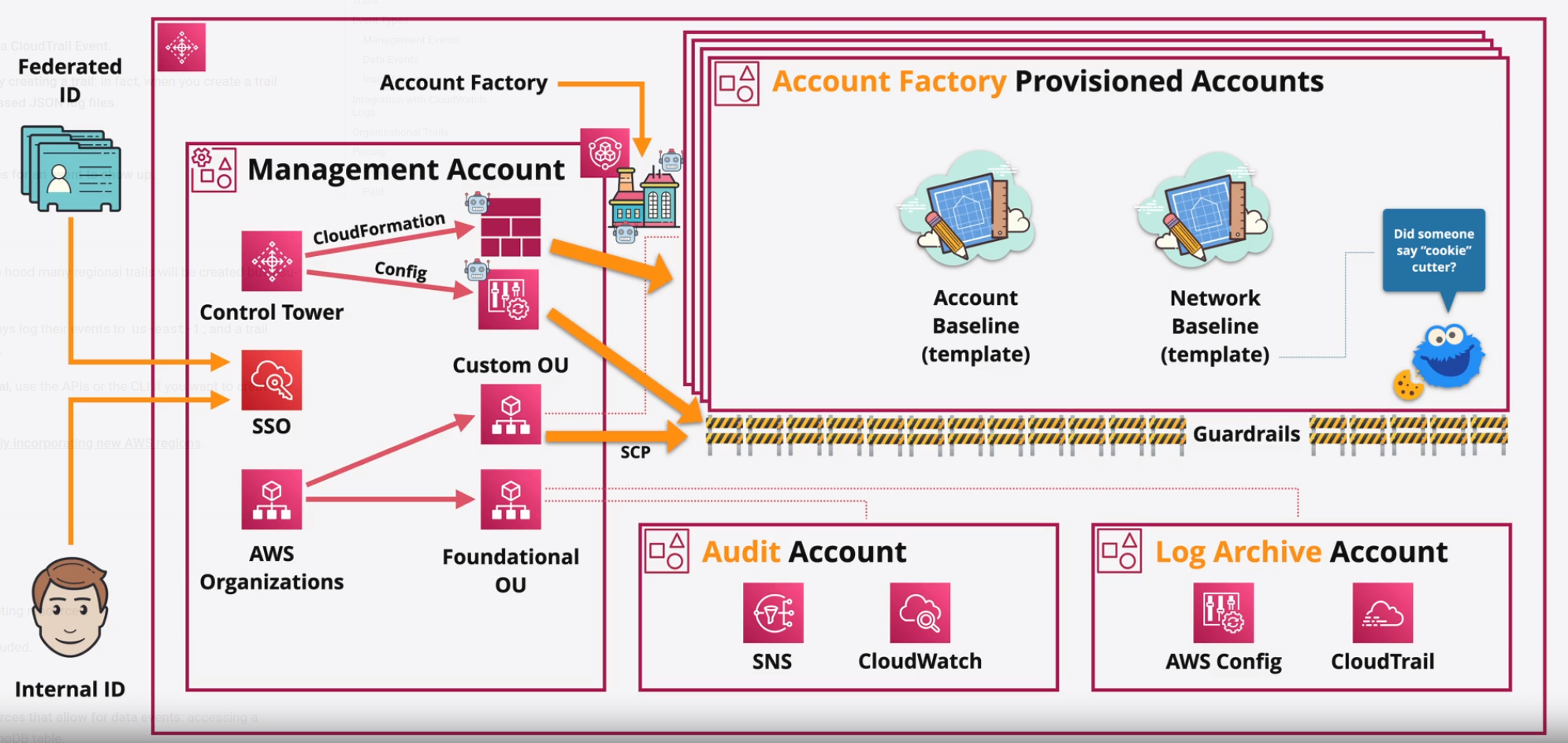
When Control Tower is first set up it generally creates two organizational units:
-
The
Foundational OU, also calledSecuritywith two accounts:-
The
Auditaccount, for users that need access to audit information. This account is also and entrypoint for third-party tools that perform auditing. Using CloudWatch Logs and SNS you can be notified about governance and security policies changes. -
The
Log Archiveaccount, for users that need access to all logging information. In this account AWS Config and CloudWatch Logs are usually used for archiving and auditing.
-
-
A
Custom OU, also calledSandbox.